 Gallery Jerimiah boys piss |
 Baseball coach gay porn |
|---|
 Additionally, some tool vendors have added enterprise-level views into their respective reporting capabilities, giving the chief information officer CIO or IT Security manager the ability to quickly see vulnerability issues across the corporation, improvements over time, and so on. It also has the advantage of making your really hire-able in two fields. In some cases, they can look for particular states, such as the ability of a process owned by a particular user ID to write to a file somewhere on the file system. These are the areas that are typically the most likely to be compromised in an attack. However, to effectively make use of these elements in a software development environment takes careful thought and clear goals. Questions Tags Users Badges Unanswered. Dradis is an open source framework for penetration testing.
Additionally, some tool vendors have added enterprise-level views into their respective reporting capabilities, giving the chief information officer CIO or IT Security manager the ability to quickly see vulnerability issues across the corporation, improvements over time, and so on. It also has the advantage of making your really hire-able in two fields. In some cases, they can look for particular states, such as the ability of a process owned by a particular user ID to write to a file somewhere on the file system. These are the areas that are typically the most likely to be compromised in an attack. However, to effectively make use of these elements in a software development environment takes careful thought and clear goals. Questions Tags Users Badges Unanswered. Dradis is an open source framework for penetration testing.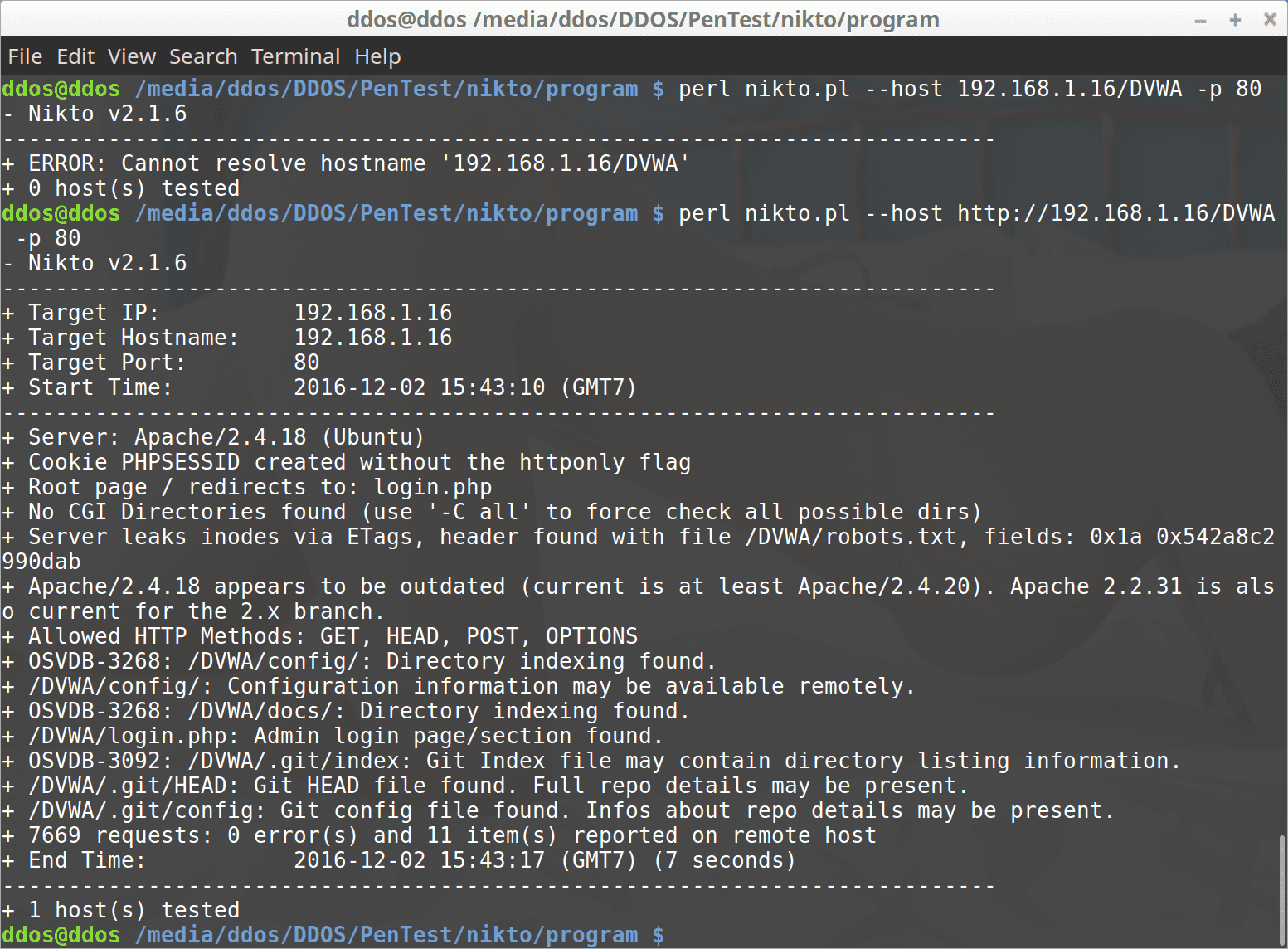
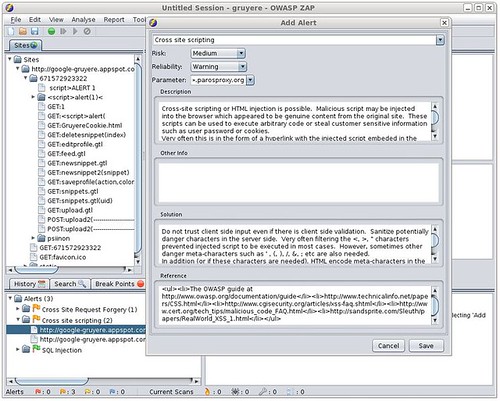
Penetration test
 Archive 167 Xbox 360 rock band nude |
 Spanking girl in bikini |
|---|


What is Penetration Testing? | Veracode
 Ilaria. Age: 18. Hello Gentlemen, |
|---|
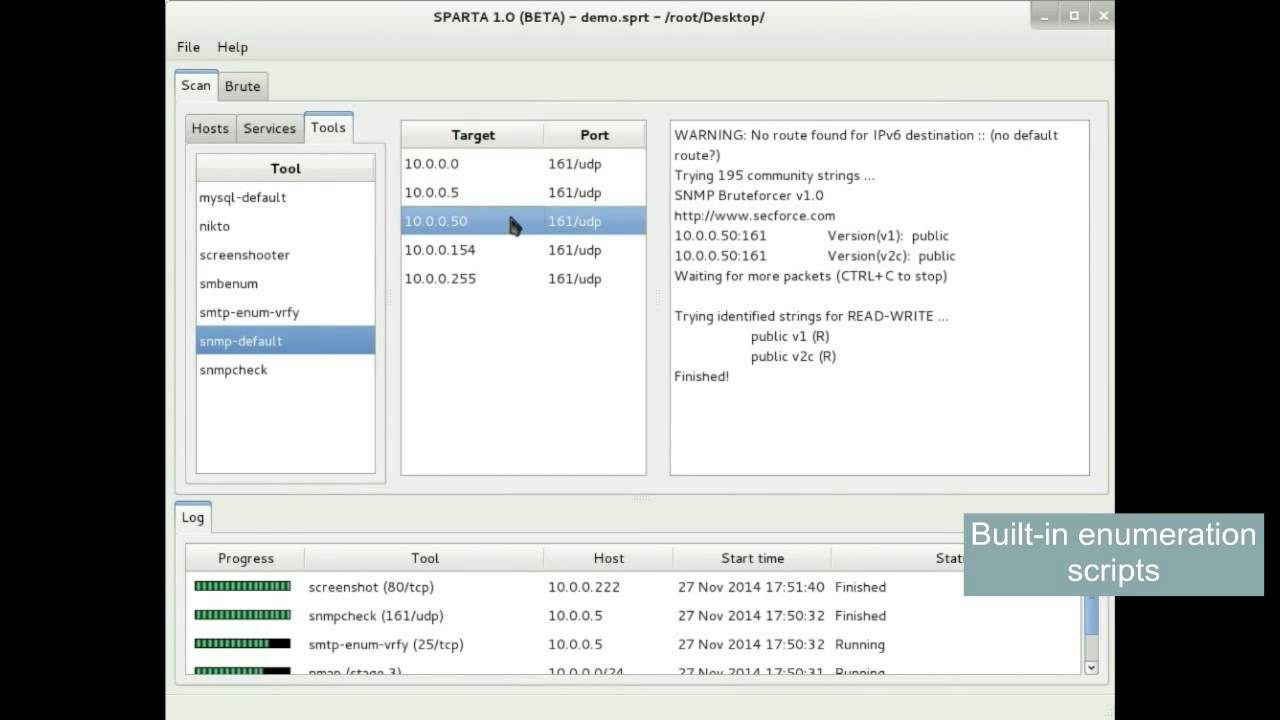


 Picture Free femdom male feminization |
 Sperm count after reverse vasctomy |
|---|
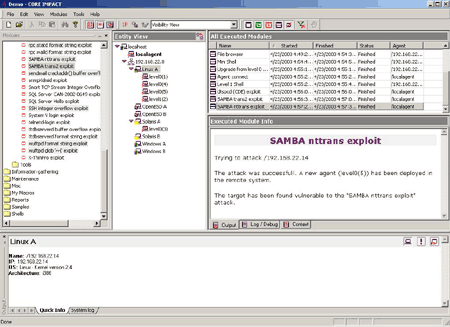
PENETRATION TESTING
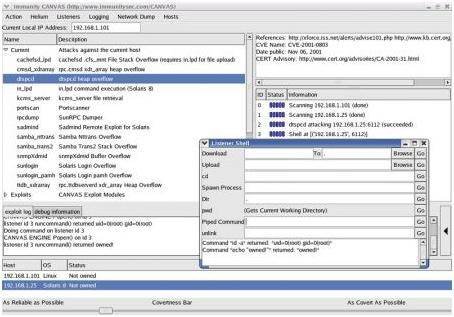
Also, the level of invasiveness involved in exploiting a vulnerability can heavily impact this step. If a design problem is detected in a penetration test—penetration testing, after all, does not distinguish between design and implementation shortcomings of the product being tested—the remediation process may require a significant engineering effort for the system to be adequately fixed. As with their host-based counterparts, they do this using a database of things that are known to be bad. These include possibly unnecessary network services being enabled, weak network services being enabled, the patch state of the network service software, and so on.

Gemma. Age: 25. I am a 22 year old Asian courtesan with a natural 34DD-25-37 figure, black silky hair and fair skin



Published: 01.08.2016 в 17:18
Similar pics:
 Easter egg roll white house gay lesbian |
 Seduced wife sex tubes |
|---|---|
 Femdom human toilet slave |
 Abused shaved twinks |
 Cable midget upright piano |
 Female domination bondage and torture stories |





